
Discover how EasyNAC protects your business, simplifies compliance, and keeps your data secure—tailored for small and medium-sized organizations.
![[background image] image of contact center space (for a data analytics and business intelligence)](https://cdn.prod.website-files.com/68373a2d00015771a42e68b9/684c7752840f7b500193bdd1_dclights2-600-q5.jpg)
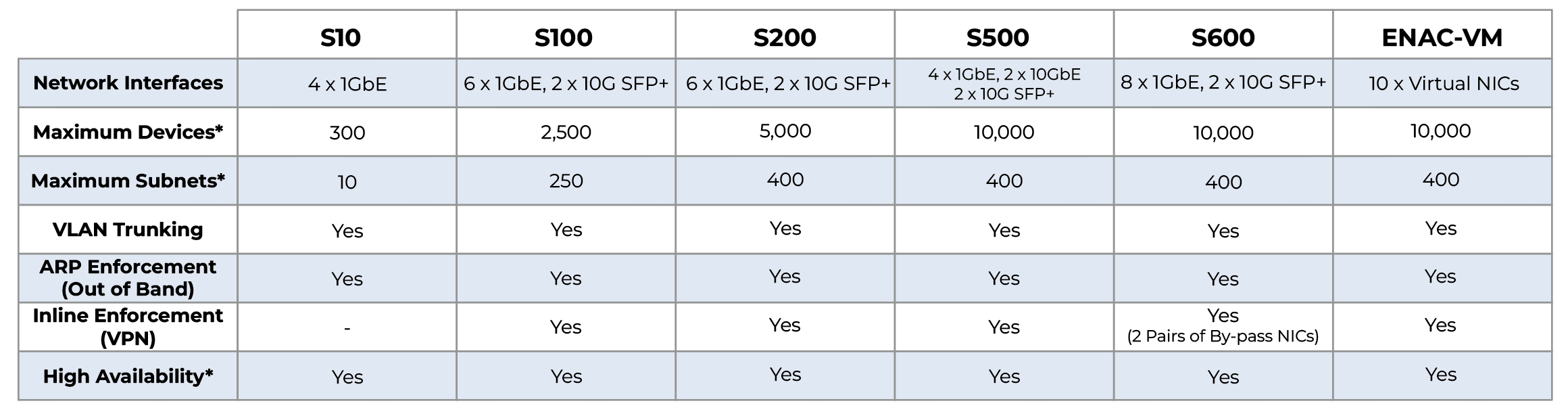
Hardened appliances that deliver plug-and-protect Network Access Control. They provide full Layer-2 visibility, ARP enforcement, device profiling, and automated threat response without requiring network changes. Available in hardware and virtual options to scale from small sites to large enterprise networks
![<subject>[interface] screenshot of collaboration interface (for a productivity tools business)</subject>](https://cdn.prod.website-files.com/68373a2d00015771a42e68b9/683747851d1551c0041320fe_5387166b-d0f5-4407-b4a6-b3a5cb9000cb.avif)
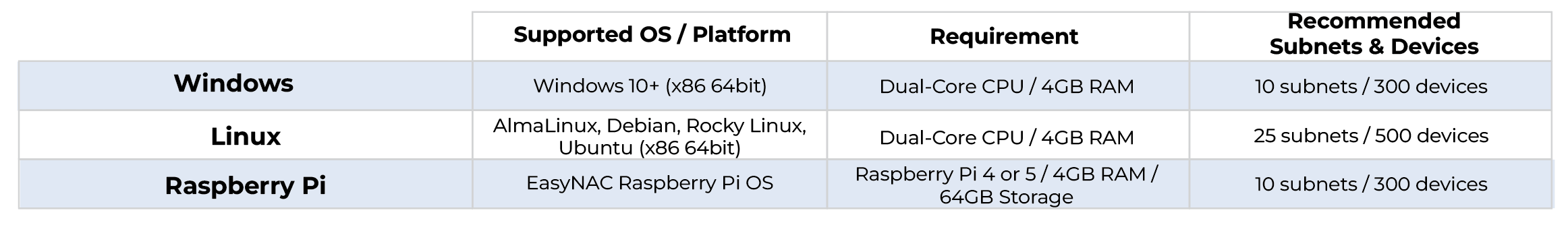
Lightweight software sensors that extend EasyNAC protection to branch offices and remote sites. Deployable on Windows, Linux, or Raspberry Pi, they report local device activity in real time and enforce ARP-based controls under EasyNAC appliance direction. Simple to install and immediately expand protection to distributed environments

Centralized management and reporting platform for multi-appliance deployments. CVM consolidates visibility, streamlines policy synchronization, automates backups, and allows license sharing across appliances. It ensures administrators maintain full oversight and consistent security across all sites

EasyNAC Server Appliances are the core of the solution, delivering full-featured, agentless Network Access Control (NAC) without network changes or endpoint configuration. They detect all devices across protected subnets, profile endpoints, and provide visualization tools so administrators can instantly see what’s on the network.
When unauthorized or non-compliant devices are detected, EasyNAC Appliances automatically quarantine or restrict access using ARP enforcement and assist with remediation. They also validate endpoint security posture, ensure BYOD devices are registered, and manage guest access. EasyNAC integrates with leading enterprise tools—including Active Directory, antivirus/XDR, patch management, cloud identity, and firewalls—to enforce security policies and automate responses.
Instantly detect and enforce policy on every device
Works with existing infrastructure; no upgrades or VLAN changes required.
Isolate compromised or suspicious devices in seconds.
Built-in reporting and audit trails simplify regulatory alignment.
Protects small offices to global enterprises with distributed deployment options.
Intuitive dashboards, automated updates, and centralized control reduce IT overhead
Automated Threat Response – Instantly quarantine or restrict compromised devices based on alerts from firewalls, XDR, SIEM, or other security solutions, reducing response time to seconds.
Trusted by organizations worldwide to secure LAN, WLAN, and VPN environments without disruption.

Enforcer Sensors bring full-featured network access control to branch and remote locations at a fraction of the cost, by integrating seamlessly with a central EasyNAC appliance.
With no configuration or network changes required, deploying Enforcer Sensors is a true drop-in solution. They extend secure network access to remote sites in minutes—even by non-IT personnel.
Choose the option that fits your needs with light-weight hardware or software-based sensors

![<subject>[interface] screenshot of collaboration interface (for a productivity tools business)</subject>](https://cdn.prod.website-files.com/image-generation-assets/26512cae-c617-4e86-9356-ceda5712c0da.avif)



![image of wireless security solutions interface [interface]](https://cdn.prod.website-files.com/image-generation-assets/ff673733-dc51-418c-acd8-e56e3359f314.avif)
Discover advanced network access control solutions for business networks. Protect your data, manage devices, and ensure compliance with ease.
![[background image] image of contact center space (for a data analytics and business intelligence)](https://cdn.prod.website-files.com/image-generation-assets/c6108207-eb8f-4df4-bf21-2ada31eda025.avif)